The Rto Ideas
S3 Backup for Dummies
Table of Contents8 Simple Techniques For Aws BackupThe 7-Minute Rule for Aws Cloud BackupAws S3 Backup - QuestionsThe Best Strategy To Use For Aws Cloud BackupThe 20-Second Trick For Ransomware Protection
Keeping numerous vendors and also platforms along with common computing has put excellent strain on IT divisions. Moving forward, information defense have to have the ability to adapt to these currently complicated situations. Data security approaches are designed to protect data, protect personal privacy and stop information loss and corruption without trading them for evaluation and also testimonial.
Information erasure strategies also verify the information can not be recuperated. Gain access to management controls make sure information stability by restricting access to digital properties. This enables granular control over which teams of people are provided accessibility to systems, and also when. Monitoring as well as securing endpoint access prolongs the reach of an information defense program by covering network-connected tools despite where they are situated.
So a lot of the globe's communications and also business takes place in the cloud or with personal devices in remote job settings. The most effective information protection solutions combine robust protection actions with human processes and process. The general objective: to make certain data security is considered early during the electronic info life process.
About Protection Against Ransomware
Data safety is every person's company, so, it's also important to make certain normal, recurring protection understanding training becomes part of your data security strategy - protection against ransomware - https://www.directorynode.com/author/clumi0/. Freelance Innovation Writer Michelle is a freelance modern technology writer. She has actually produced technological web content for a range of brand names and publications, including Company Insider, DICE, GE Dig ...
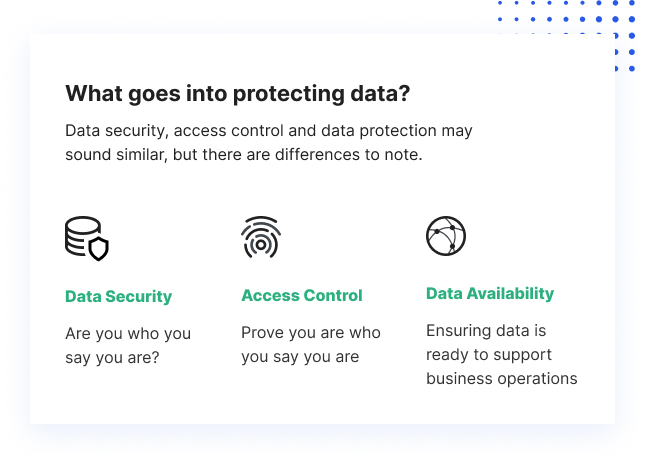
The terms information protection and information personal privacy are commonly used mutually, but there is an essential distinction in between the two. Data personal privacy specifies that has access to information, while data protection gives devices and also plans to actually limit access to the information (https://www.businessdocker.com/author/clumi0/). Compliance guidelines help make certain that individual's personal privacy demands are performed by companies, and companies are accountable to take steps to safeguard personal individual information.
It plays a crucial duty in company procedures, development, and also funds. Data security options count on technologies such as data loss prevention (DLP), storage space with integrated information security, firewall softwares, encryption, as well as endpoint defense.
A data protection approach is vital for any kind of organization that gathers, takes care of, or shops delicate data. Information security principles help shield information and also make it offered under any kind of circumstances.
Aws S3 Backup - The Facts
Below are crucial data administration elements pertinent to information protection: ensuring customers can access as well as make use of the information required to execute organization even when this information is shed or harmed. involves automating the transmission of vital information to offline as well as on-line storage space. entails the evaluation, cataloging, and defense of information properties from various resources, including facility outages as well as interruptions, application and customer mistakes, device failing, and malware as well as infection assaults.
Information privacy is normally related to individual wellness info (PHI) and also personally recognizable information (PII). This includes financial details, medical documents, social security or ID numbers, names, birthdates, and also contact details. Data privacy issues put on all delicate information that organizations manage, consisting of that of consumers, shareholders, and staff members. Usually, this information plays an important function in organization operations, development, and financial resources.
It prevents criminals from having the ability to maliciously utilize information as well as aids make certain that companies fulfill governing needs. Data protection policies govern how certain information types are gathered, transferred, and also made use of. Individual information includes various kinds of information, consisting of names, pictures, email addresses, savings account information, IP addresses of desktop computers, as well as biometric data.
The Definitive Guide for Ransomware Protection
Additionally, each legislation has many conditions that may use to one case yet not another, as well as all policies go through adjustments. This level of intricacy makes it hard to apply conformity constantly and also suitably. Both data security and also privacy are vital and also the 2 typically come together, these terms do not represent the exact same point.
Information personal privacy defines the policies that information security devices and processes use. Developing data personal privacy standards does not ensure that unauthorized individuals don't have accessibility. Similarly, you can limit accessibility with data defenses while still leaving sensitive data prone. Both are required to ensure that data continues to be safe and secure. An additional essential difference between personal privacy and also protection is who is commonly in control.
For defense, it is up to the companies dealing with data to ensure that it stays private. Compliance laws mirror this distinction and are developed to assist make sure that individuals' personal privacy requests are passed by firms. When it comes to safeguarding your information, there are many storage space and also monitoring options you can select from (protection against ransomware).
Below are several of the most typically made use of practices as well as technologies: a very first action in data security, this entails discovering which data collections exist in the organization, which of them are company important and also which has sensitive data that may be subject to conformity regulations (aws backup). a set of approaches as well as devices that you can make use of to stop data from being swiped, lost, or unintentionally removed.
Aws Backup Fundamentals Explained
modern-day storage space devices offers built-in disk clustering and redundancy. Cloudian's Hyperstore provides up to 14 nines of longevity, reduced expense enabling storage of big quantities of information, as well as fast accessibility for marginal RTO/RPO. Find out more in our guide to. produces copies of data and shops them independently, making it feasible to recover the data later on in instance of loss or adjustment.